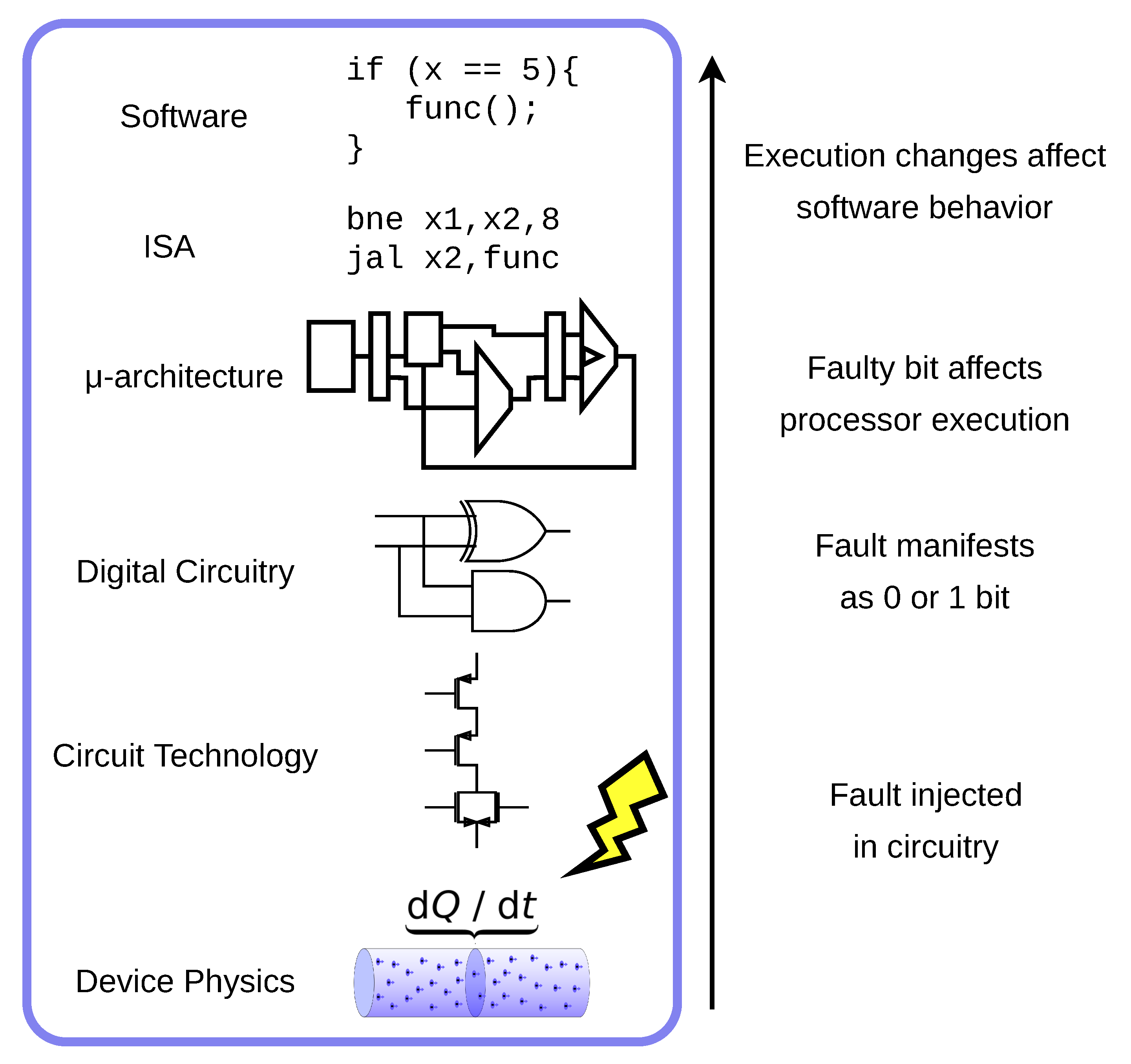
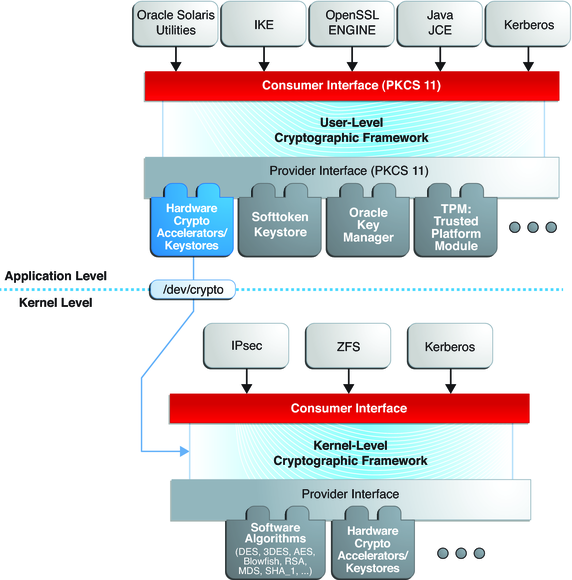
Google Cloud Designs Hardware Module for Encryption, Sold as a Service | Data Center Knowledge | News and analysis for the data center industry
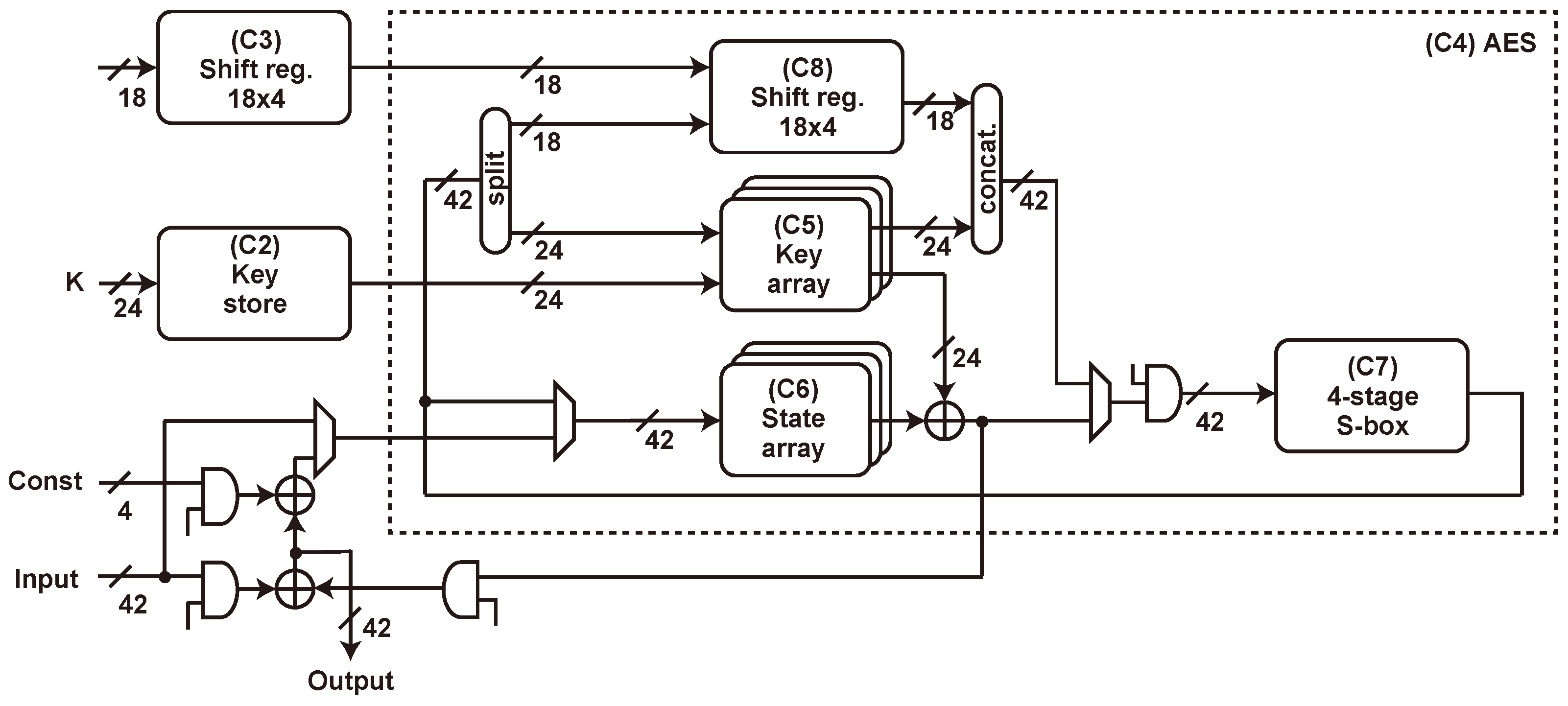
Cryptography | Free Full-Text | Hardware Performance Evaluation of Authenticated Encryption SAEAES with Threshold Implementation