![Keenetic DSL (black) and Intel Dual Band Wireless Adapter-AC 3165 - 2.11 [legacy] - Keenetic Community Keenetic DSL (black) and Intel Dual Band Wireless Adapter-AC 3165 - 2.11 [legacy] - Keenetic Community](https://content.invisioncic.com/r270260/monthly_2021_03/2021-03-07_133803.png.dbcab11b40de0f7982eaaa2dc4c1b55b.png)
Keenetic DSL (black) and Intel Dual Band Wireless Adapter-AC 3165 - 2.11 [legacy] - Keenetic Community
![Keenetic DSL (black) and Intel Dual Band Wireless Adapter-AC 3165 - 2.11 [legacy] - Keenetic Community Keenetic DSL (black) and Intel Dual Band Wireless Adapter-AC 3165 - 2.11 [legacy] - Keenetic Community](https://content.invisioncic.com/r270260/monthly_2021_03/2021-03-07_133645.png.f6bbe874b066e766478f12f6a9719d55.png)
Keenetic DSL (black) and Intel Dual Band Wireless Adapter-AC 3165 - 2.11 [legacy] - Keenetic Community

Connectivity prolems with error message --- 6105 - deauth after EAPOL key exchange sequence | Wireless Access

local-eap-server authentication eap-phase-one enable - WLAN AC V200R019C00 Command Reference - Huawei

The first deadlock vulnerability in 802.11w. The adversary listens for... | Download Scientific Diagram

Multi-Channel Man-in-the-Middle attacks against protected Wi-Fi networks: A state of the art review - ScienceDirect

WLAN by german engineering | All about Wireless LAN (IEEE 802.11) from a german/european perspective

Multi-Channel Man-in-the-Middle attacks against protected Wi-Fi networks: A state of the art review - ScienceDirect

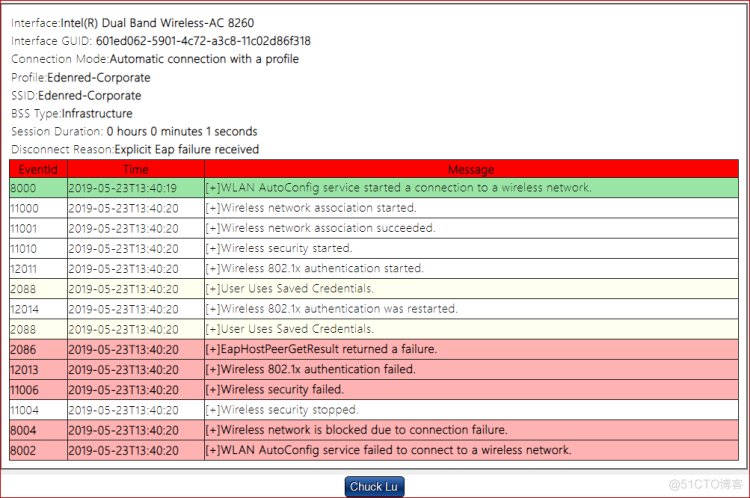

![en[EVENT6105] deauth after EAPOL key exchange sequence | SC2 en[EVENT6105] deauth after EAPOL key exchange sequence | SC2](https://1.bp.blogspot.com/-uMgNzbh8_XU/XR_nmpkpmeI/AAAAAAAAHMo/z__p9X3NoewDujgcqyZJLoT6JqfWUXueACLcBGAs/s600-rw/Device-IntelAC8260.png)