![MS-RPCE]: Packet Sequence for Secure, Connection-Oriented RPC Using NTLM as Security Provider | Microsoft Learn MS-RPCE]: Packet Sequence for Secure, Connection-Oriented RPC Using NTLM as Security Provider | Microsoft Learn](https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-rpce/ms-rpce_files/image023.png)
MS-RPCE]: Packet Sequence for Secure, Connection-Oriented RPC Using NTLM as Security Provider | Microsoft Learn

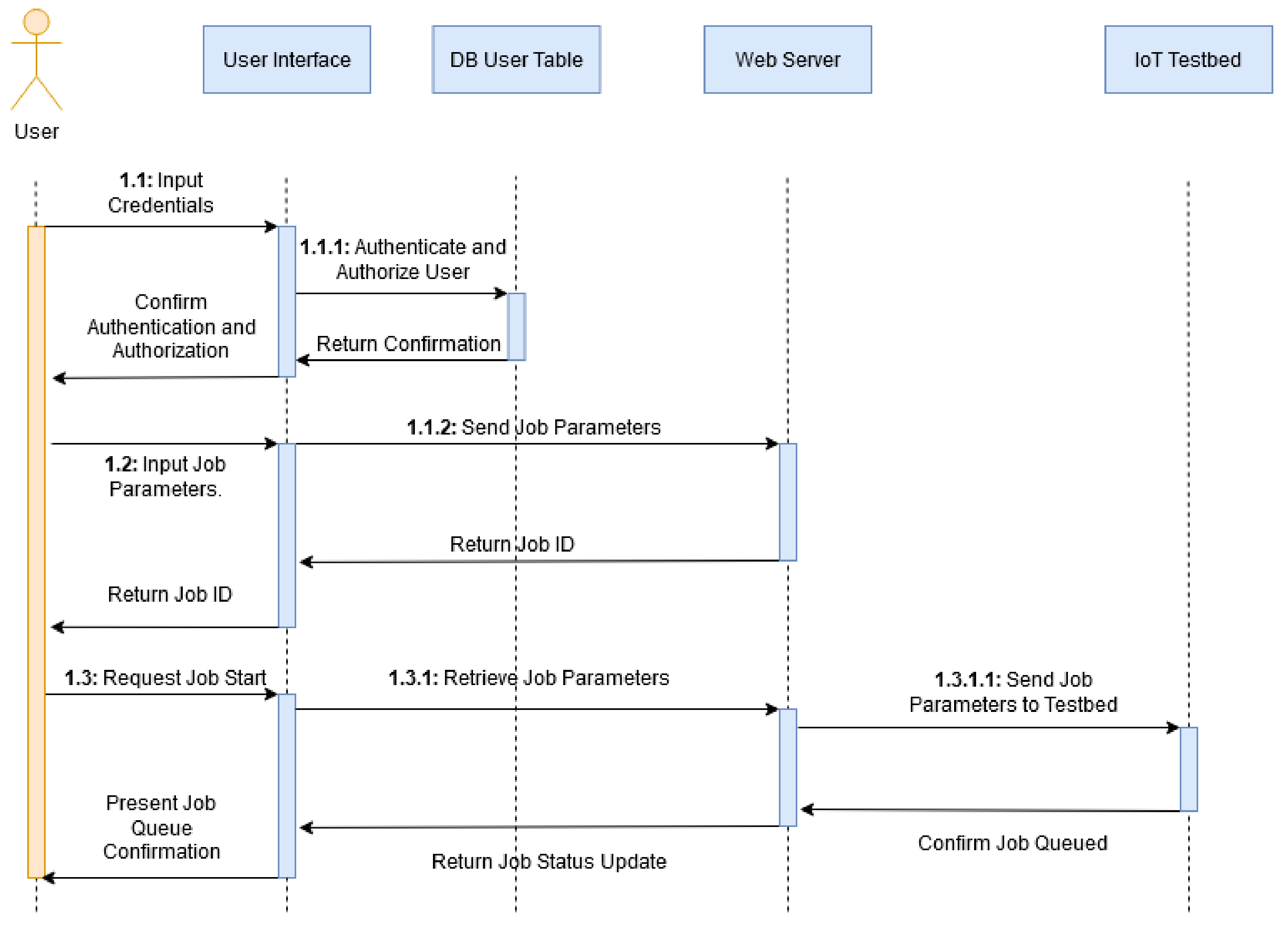
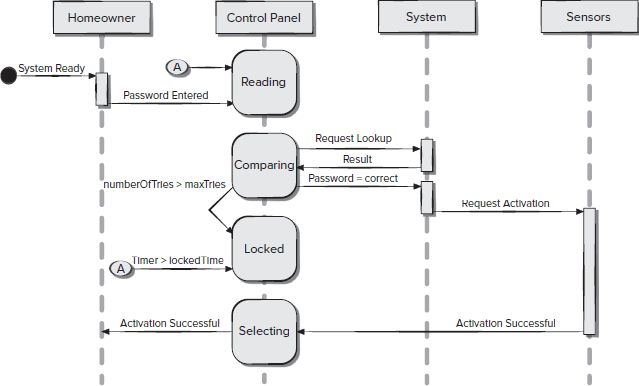
An Authentication-Oriented Approach to Model the Crosscutting Constraints in Sequence Diagram Using Aspect OCL

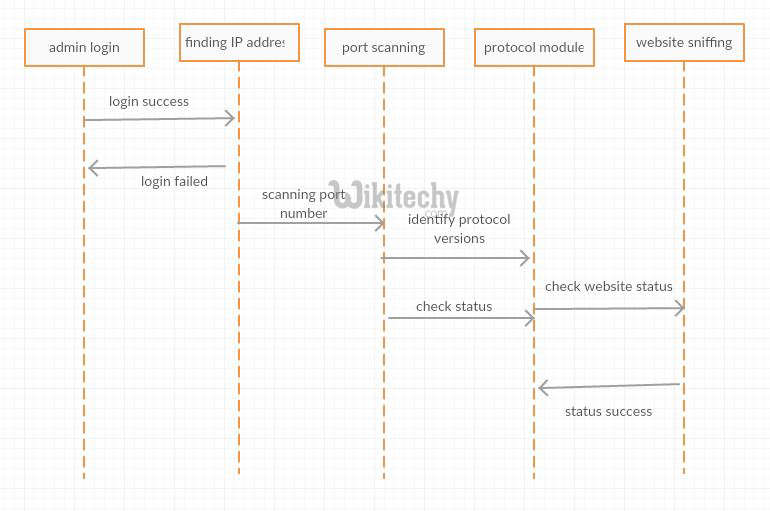
Sequence diagram of security management system (no security violation). | Download Scientific Diagram

Corporate Security And Risk Management Determine Sequence Phases For Threat Attack Ideas PDF - PowerPoint Templates
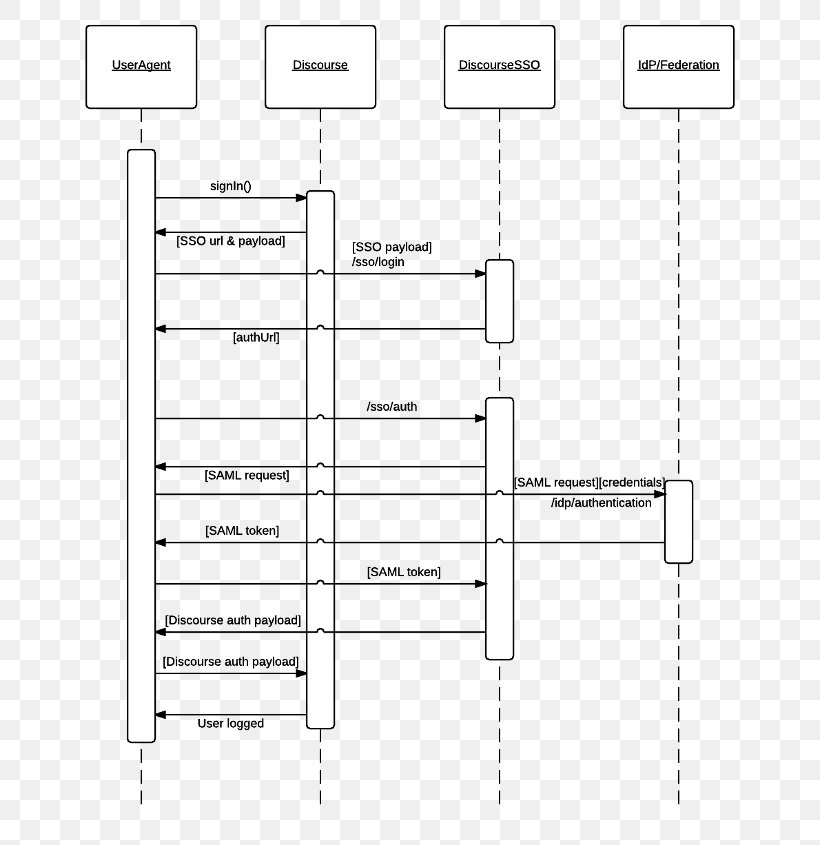
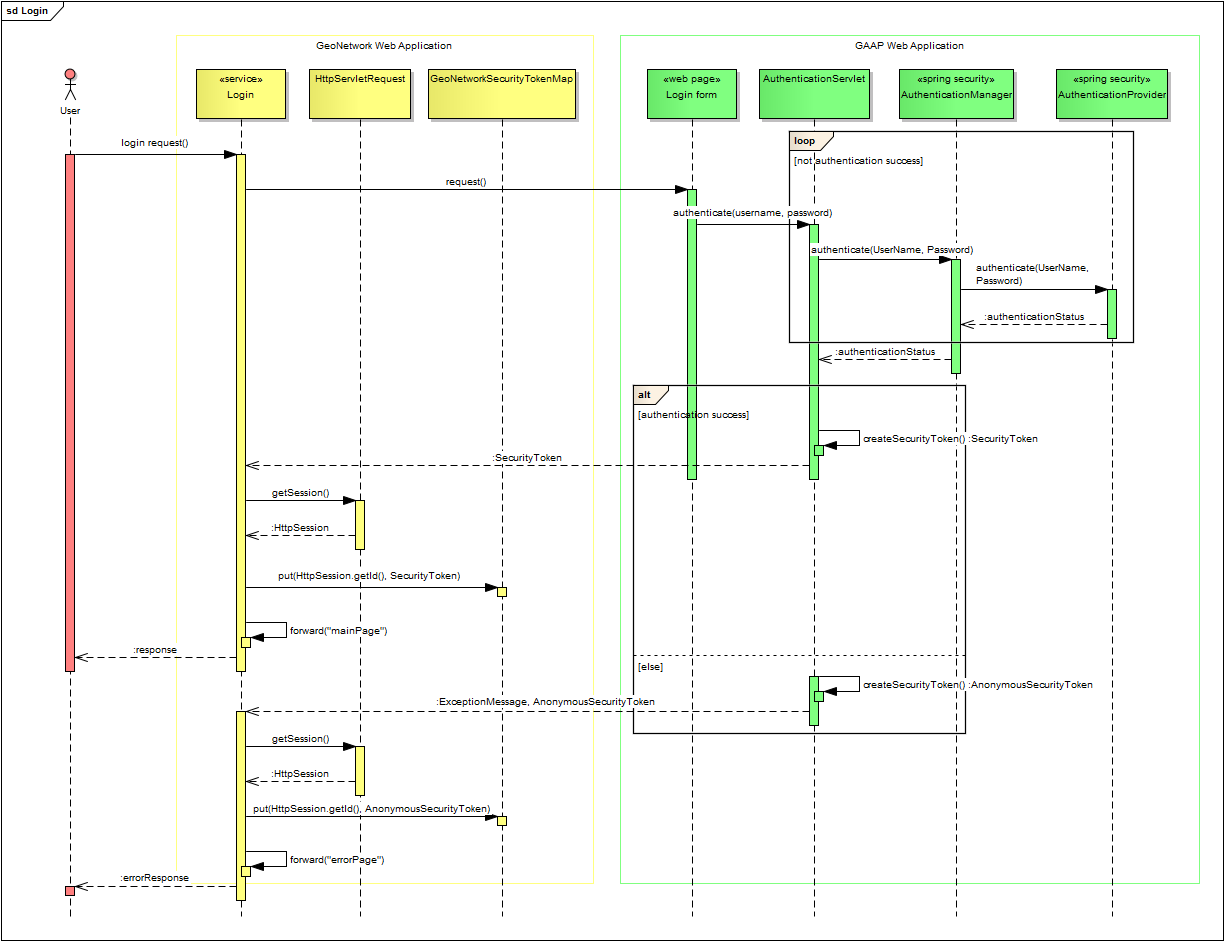
Security-token, E-Authentifizierung Sequenzdiagramm Unified Modeling Language Schaltplan - authentifizieren png herunterladen - 1700*879 - Kostenlos transparent Text png Herunterladen.

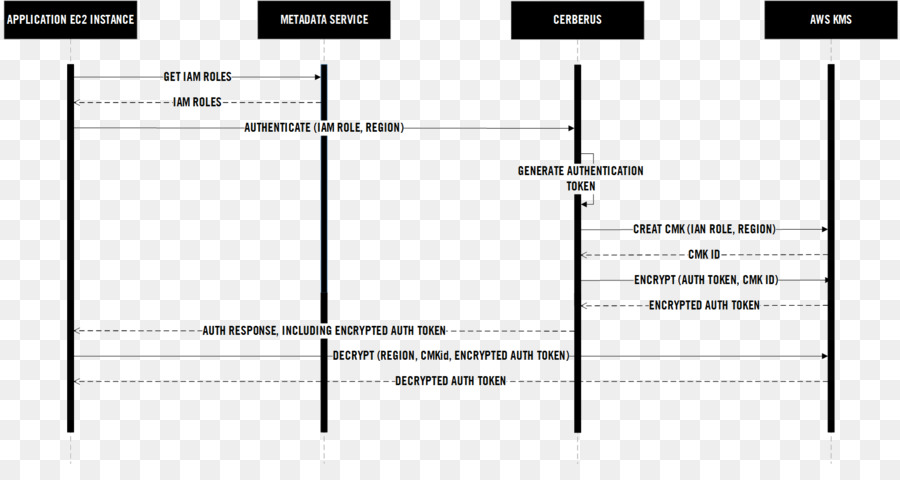
task #6118: evaluate spring-security-auth2 and spring-cloud-security as a framework for OAuth2 - EDIT - EDIT Project Management

Computer Security, Privacy, and DNA Sequencing: Compromising Computers with Synthesized DNA, Privacy Leaks, and More | USENIX