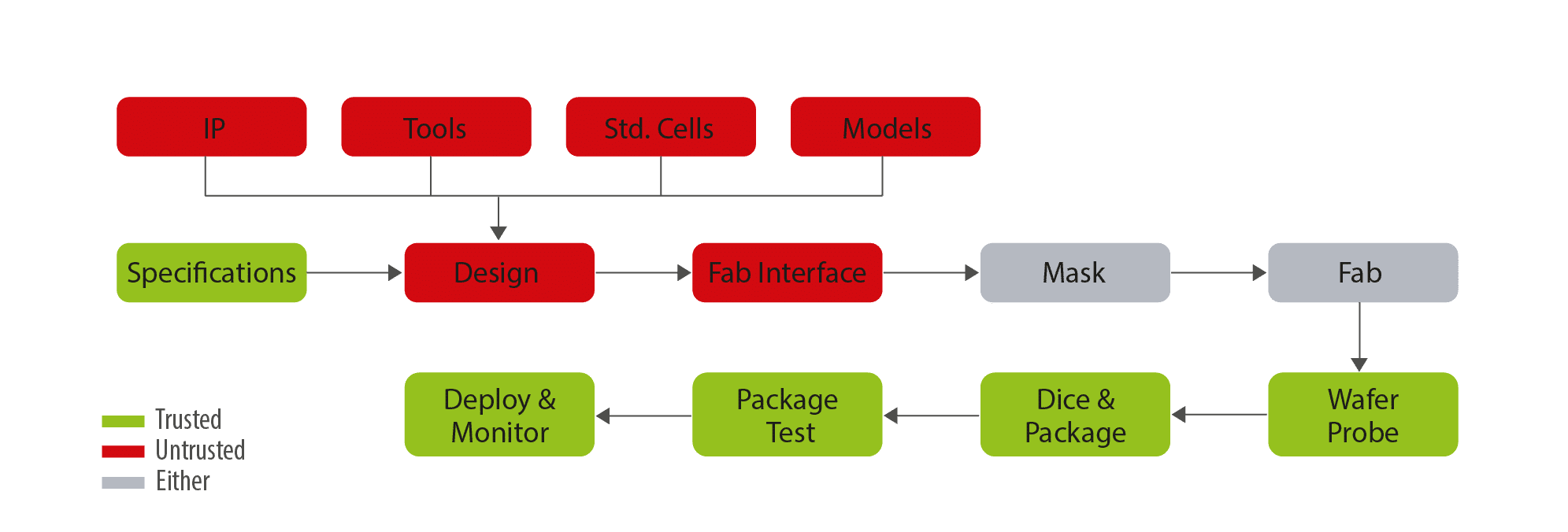
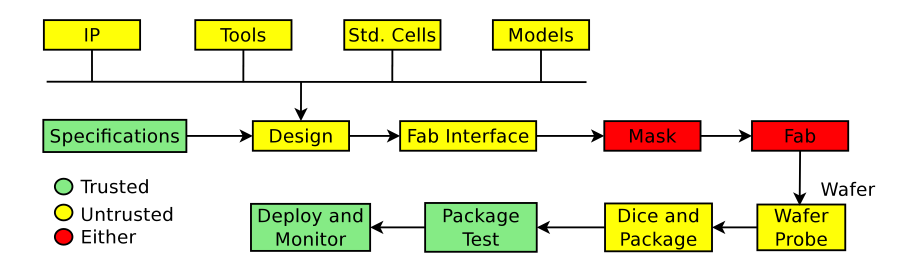
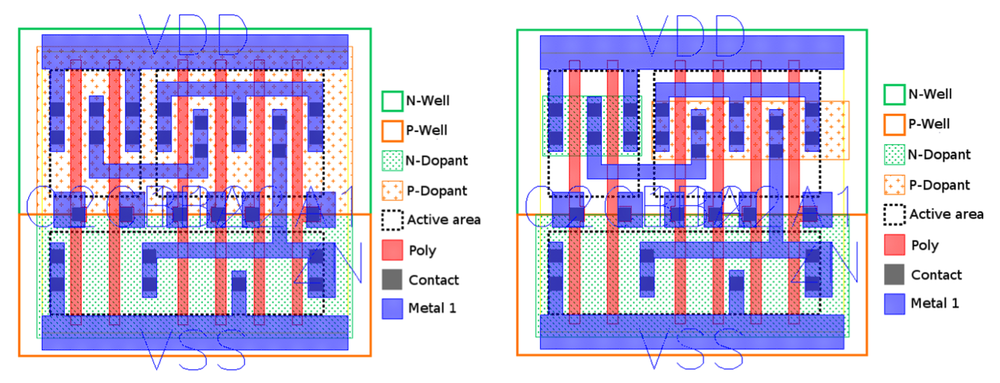
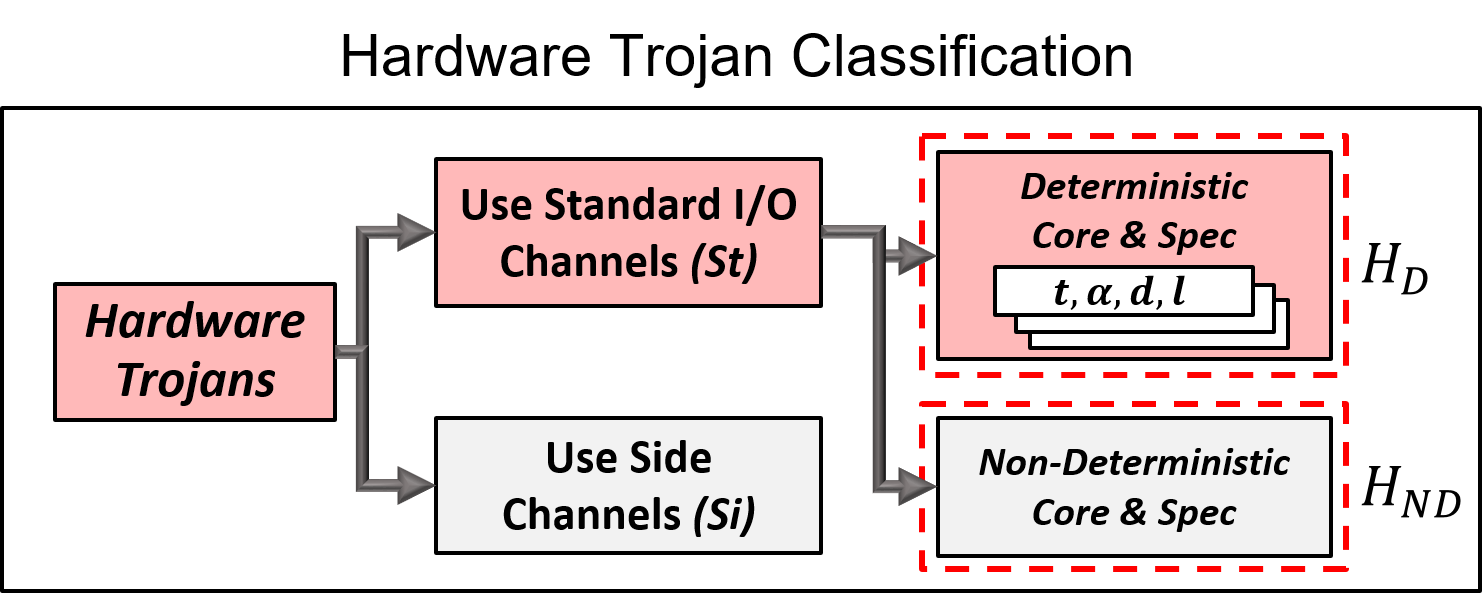
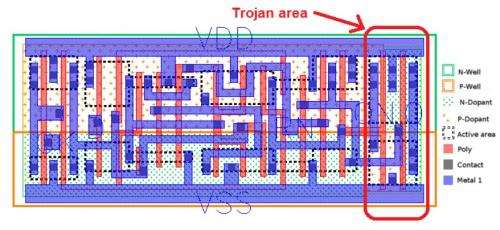
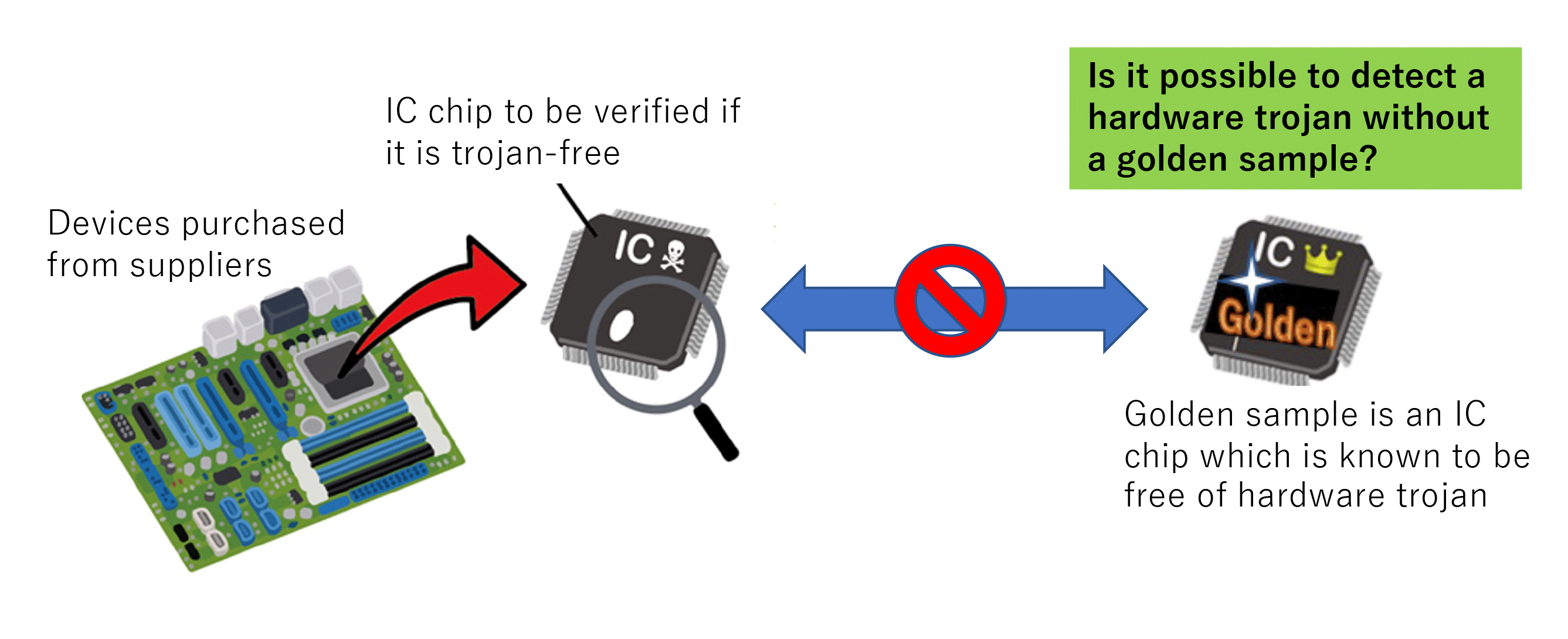
Detecting Hardware Trojans Inserted by Untrusted Foundry Using Physical Inspection and Advanced Image Processing | SpringerLink
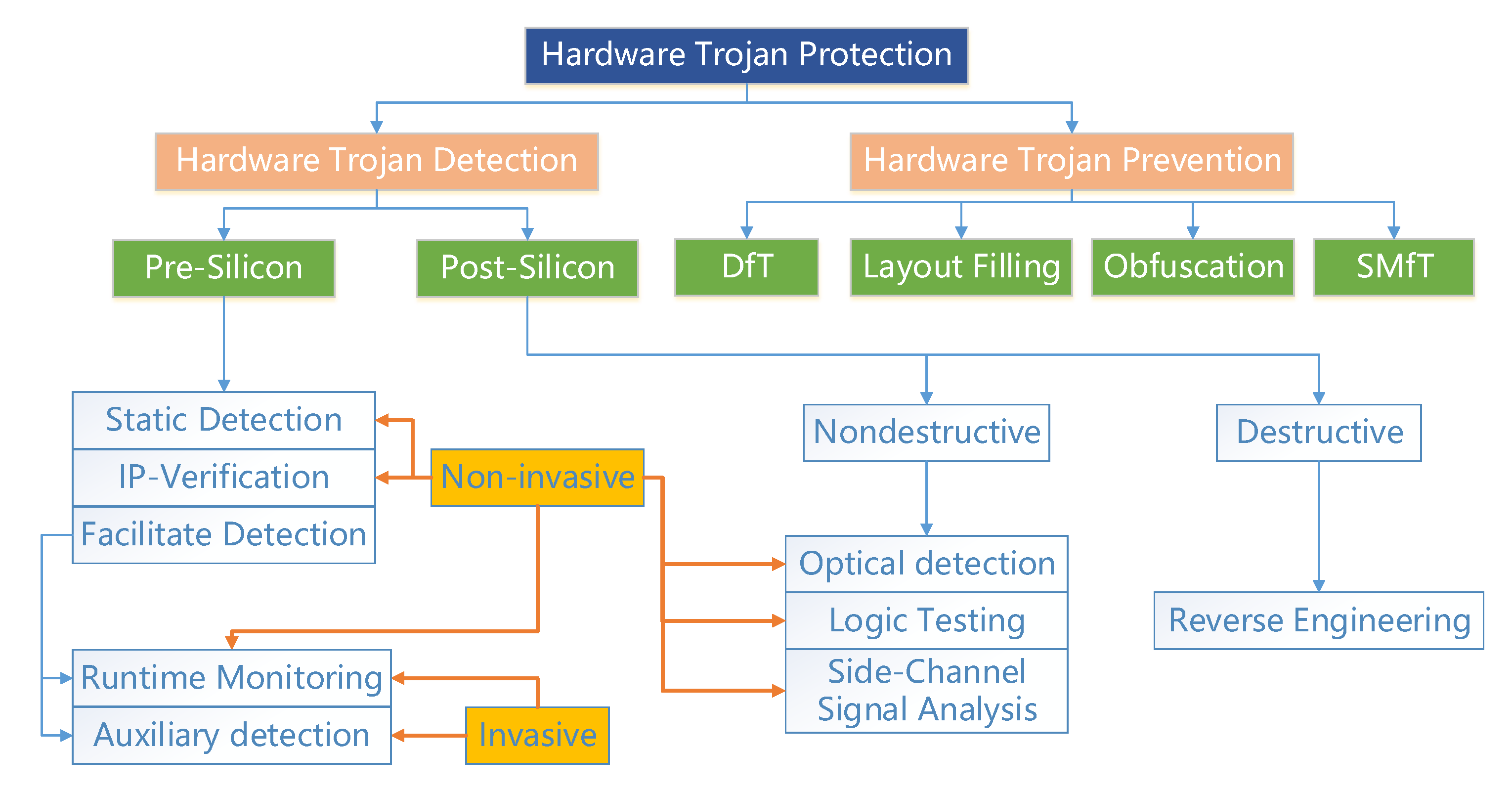
Research on hardware Trojan - Research | Hardware security research team | Cyber physical security reserch cente

Forschung im Kampf gegen Cyberangriffe durch Hardware-Trojaner | EPoCH Project | Results in brief | H2020 | CORDIS | European Commission
Improved Test Pattern Generation for Hardware Trojan Detection using Genetic Algorithm and Boolean Satisfiability





![PDF] Trustworthy Hardware: Identifying and Classifying Hardware Trojans | Semantic Scholar PDF] Trustworthy Hardware: Identifying and Classifying Hardware Trojans | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/4d9d3df6f23afef5605ae45b46deb30ffe13894f/3-Figure1-1.png)